dev-resources.site
for different kinds of informations.
What is a Three-Way Handshake?
Introduction of Three-Way Handshake
The three-way handshake, also known as the TCP handshake, is a method used in network communication protocols, particularly in the TCP (Transmission Control Protocol). It involves the exchange of three distinct messages between the client and server to guarantee a secure and synchronized connection before data transmission begins.
The TCP handshake process sets up initial sequence numbers (IPs) and synchronizes both ends of the connection before data transmission begins. It also helps to detect errors, guarantees data integrity, and provides flow control mechanisms to manage different network conditions.
Three-Way Handshake Process
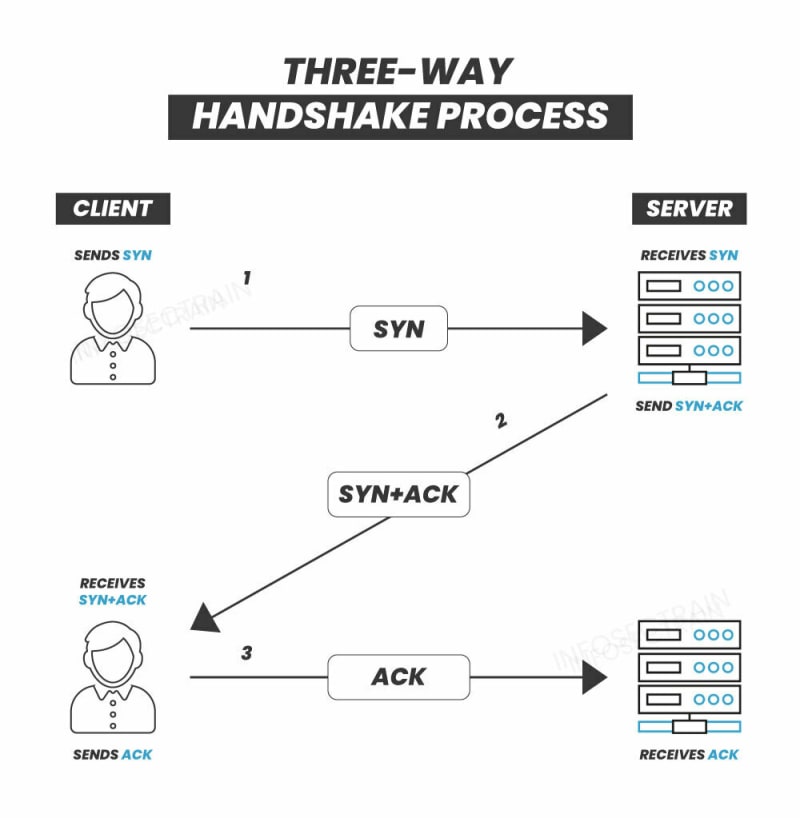
Here are the three steps of how the three-way or TCP handshake process works:
1. SYN (Synchronize): To initiate a connection, a client sends a SYN (Synchronization) packet to the server. This SYN packet contains a unique sequence number that identifies the connection. The client then sets the SYN flag to 1 to signify that it wants to initiate a connection.
2. SYN-ACK (Synchronize-Acknowledge): In response to the SYN packet, the server sends a SYN-ACK packet to acknowledge the client's request. By setting the SYN and ACK flags to 1, the server indicates it agrees to establish a connection. The server also generates a sequence number for each connection.
3. ACK (Acknowledge): Eventually, in response to the server's acknowledgment, the client sends an ACK packet with the ACK flag set. This packet's acknowledgment number is greater than the sequence number in the server's SYN-ACK packet by one. The connection is established at this stage, and the client and server may proceed to exchange data.
Once the three-way handshake is completed, the client and server may start the actual data exchange. Throughout the connection, TCP ensures that data packets are delivered correctly in the right order and retransmits any packets lost or corrupted.
How can InfosecTrain Help?
InfosecTrain’s Network Security training course helps you gain a solid foundation in network protocols like TCP and the three-way handshake. The course can give you a deeper understanding of the three-way handshake process and its significance in establishing secure and reliable network connections. We offer practical demonstrations or lab exercises to help you visualize and experience the three-way handshake process.
Featured ones: